Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

Blog – Cyber Physical Risk Academy
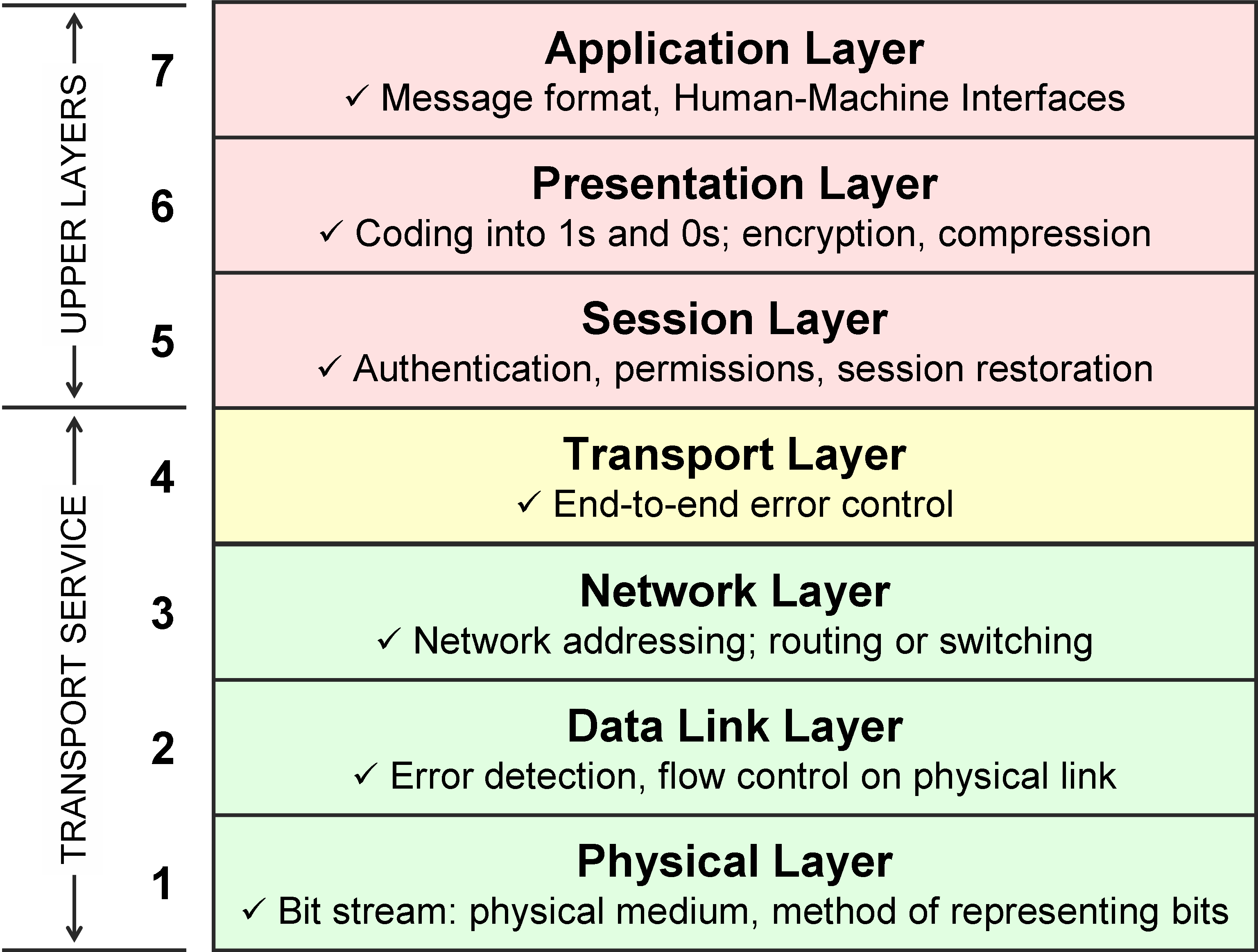
osi model explanation

Blog – Cyber Physical Risk Academy
Glossaries learnonline

A survey of cyber security threats and solutions for UAV

Securing Layer 8 – Open Sourcerers
How VMware can Secure Mobile Endpoints with Threat Defense (MTD

Stateful Inspection - FasterCapital
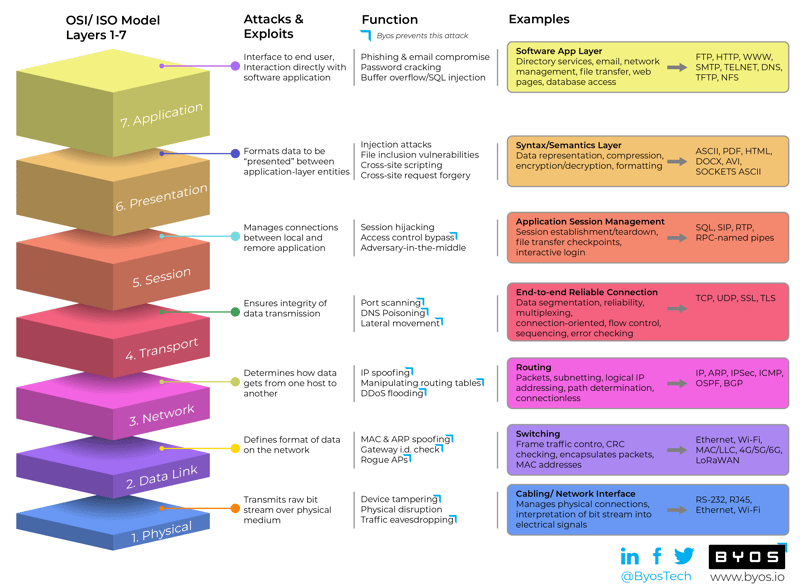
How Cyber Adversaries Attack Each of the OSI Layers 1-7

OSI Model: The 7 Layers of Network Architecture – BMC Software

Cyber Hygiene and the Cyber Ecosystem Attack Analysis Methodology

A Framework to Protect Data Through Segmentation

Security Threats at OSI layers

Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

Major Network Fundamental is Explained. OSI Model and Its Security